Our Product
Our Products
We offer both IP-based and Analog CCTV Systems to meet diverse  surveillance needs:
surveillance needs:
IP CCTV Systems: Advanced, high-resolution cameras with real-time monitoring.
Remote access via smartphones, tablets, or PCs.
Integration capabilities with existing network infrastructure.
Ideal for large-scale installations requiring scalability and superior image quality.
Analog CCTV Systems: Reliable and cost-effective surveillance solutions.
Easy to install and maintain, suitable for small to medium-sized setups.
Provides clear video output for basic monitoring requirements.
Both systems ensure enhanced security and monitoring for residential, commercial, and industrial applications.
Our Biometric Attendance System is a cutting-edge solution for efficient and secure workforce management. It uses advanced biometric technology to accurately track employee attendance and eliminate the possibility of proxy or manual errors. 
Key Features:
- Accurate Identification: Utilizes fingerprint, facial recognition, or other biometric modalities for precise employee authentication.
- Seamless Integration: Easily integrates with payroll systems for automated processing.
- Real-Time Tracking: Monitors attendance and generates instant reports for management.
- Data Security: Ensures secure storage and management of sensitive employee data.
- User-Friendly Interface: Simple to operate and maintain for businesses of all sizes.
Applications:
Perfect for offices, factories, schools, and other organizations to enhance efficiency and maintain attendance records effortlessly.
Our Access Control Systems are designed to provide secure and efficient management of entry and exit points, ensuring only authorized personnel can access specific areas. These systems enhance security and streamline operations across various sectors.
 Hand using security key card unlocking the door to entering private building . Home and building security system[/caption]
Hand using security key card unlocking the door to entering private building . Home and building security system[/caption]
Key Features:
- Authentication Methods: Supports a range of technologies, including RFID cards, biometric identification (fingerprint, facial recognition), PIN codes, or a combination for multi-factor authentication.
- Customizable Access Levels: Allows user-specific permissions based on roles and responsibilities.
- Real-Time Monitoring: Tracks access logs and provides real-time updates for enhanced oversight.
- Integration Ready: Easily integrates with existing security systems, including surveillance cameras and fire alarms.
- Remote Access Management: Enables administrators to control and monitor access remotely.
Applications:
Perfect for offices, factories, educational institutions, healthcare facilities, data centers, and residential complexes to ensure a safe and controlled environment.
Our Fire Alarm Systems are designed to provide reliable, early detection and warning of fire hazards, ensuring the safety of people, property, and assets. These systems are essential for prompt action in emergencies and meet the highest industry standards. 
Key Features:
- Early Detection: Advanced sensors detect smoke, heat, or flames to minimize response time.
- Alarm Notification: Audible and visual alerts for immediate evacuation and awareness.
- Customizable Solutions: Configurable for different building types and sizes.
- Integration Capabilities: Seamlessly integrates with sprinkler systems, emergency lighting, and other safety protocols.
- Compliance Certified: Meets local and international fire safety standards.
Applications:
Ideal for commercial buildings, residential complexes, factories, schools, hospitals, and public spaces requiring robust fire safety measures.
EPABX System (Electronic Private Automatic Branch Exchange)
Our EPABX Systems offer advanced telecommunication solutions for seamless internal and external communication within organizations. Designed for efficiency, they streamline call management and enhance connectivity across departments. 
Key Features:
- Efficient Call Routing: Automatically routes calls to the desired extensions without manual intervention.
- Multiple Line Management: Supports multiple incoming and outgoing lines for uninterrupted communication.
- Intercom Functionality: Enables quick and direct communication between internal extensions.
- Customizable Features: Includes call forwarding, conferencing, voicemail, and call recording options.
- Scalable Solutions: Easily expandable to accommodate growing organizational needs.
- User-Friendly Interface: Intuitive and easy to operate, suitable for businesses of all sizes.
Applications:
Ideal for corporate offices, hotels, hospitals, educational institutions, and any organization requiring efficient and cost-effective telecommunication systems.
A Public Announcement (PA) System is a communication system used to broadcast messages, warnings, or information to a large group of people in a specific area, such as a building, campus, city, or any public space. It typically consists of several components that work together to ensure clear and effective communication.
Key Components of a PA System:
- Microphone: The device used by the speaker to input sound into the system. It can be handheld, wireless, or mounted for hands-free operation.
- Amplifier: This device increases the volume of the microphone signal, making it loud enough to reach a wide audience.
- Speakers: These are the output devices that project the sound to the listeners. They can be placed strategically throughout the area to ensure even distribution of sound.
- Mixer: In more complex systems, a mixer allows the user to adjust sound levels and combine various audio sources (e.g., microphones, background music).
- Audio Sources: This includes any other audio devices that might be part of the system, such as a media player, radio, or pre-recorded announcements.
- Cabling and Connectivity: These include wires and connectors that link all the components together. In modern systems, wireless setups are also common.
- Control Console: This is the central unit where operators can manage the PA system, including turning it on/off, adjusting volume, and selecting input sources.
Types of PA Systems:
- Wired PA Systems: Use cables to connect microphones, amplifiers, and speakers.
- Wireless PA Systems: Use radio frequency signals to transmit sound between components without physical wires, offering flexibility in setup.
- Integrated PA Systems: These are built into other devices or infrastructures, such as in schools, stadiums, or airports.
Applications of PA Systems:
- Emergency Alerts: Used to broadcast emergency messages during crises, like fires, natural disasters, or terrorist threats.
- Public Events: For announcements during events, rallies, concerts, and conferences.
- Commercial Use: In stores, malls, and businesses to play background music or communicate promotions.
- Transportation Hubs: Airports, train stations, and bus terminals use PA systems to announce departures, arrivals, and important safety information.
- Education: In schools or universities, PA systems are used to communicate between administrators and students, especially in emergencies or for general announcements.
The effectiveness of a PA system depends on factors like sound clarity, coverage area, ease of use, and maintenance. Modern PA systems can also integrate with digital technology, enabling automated announcements, live streaming, and other advanced functionalities.
A Video Door Phone (VDP), also known as a Video Door Intercom, is a security system that allows the residents of a building or house to visually identify visitors at the door before granting them access. It combines audio and video communication, allowing for two-way interaction between the person at the door and the person inside the building.
Key Components of a Video Door Phone System:
- Outdoor Unit (Door Station):
- Camera: A video camera is installed at the door or entrance area. It captures the image of the visitor and sends the video feed to the indoor unit.
- Microphone and Speaker: These allow the visitor to communicate with the person inside. The microphone picks up sound from the visitor, while the speaker lets the person inside hear the visitor’s voice.
- Button/Access Control: The visitor can press a button to alert the resident that they are outside. This unit may also have a built-in intercom or additional security features like a keypad for entering codes or even biometric scanners for secure access.
- Indoor Unit (Receiver/Monitor):
- Monitor/Screen: This displays the live video feed from the outdoor camera, allowing the person inside to see who is at the door.
- Microphone and Speaker: These enable two-way communication with the visitor, so the resident can talk to the person at the door.
- Control Buttons/Touchscreen: The indoor unit typically has buttons or a touchscreen to control functions such as answering the door, unlocking the door remotely, adjusting volume, and managing settings like brightness or contrast of the video feed.
- Power Supply: The video door phone system needs a power source for both the outdoor and indoor units. It can be powered through mains electricity, batteries, or even by using Power over Ethernet (PoE) technology in more advanced systems.
- Connectivity:
- Wired Systems: These systems use cables to connect the outdoor and indoor units. It is more stable but may require more installation work.
- Wireless Systems: These systems use Wi-Fi or other wireless communication methods to transmit video and audio signals. They offer more flexibility in installation and are easier to set up in places where running wires is difficult.
A Digital Door Phone (DDP), also known as a Digital Door Intercom, is an advanced security system that allows two-way communication between the person at the entrance (visitor) and the person inside a building, similar to a video door phone but typically with more integrated digital features. Digital door phones utilize digital technology to transmit audio and video signals, providing higher clarity, security, and more flexible features compared to analog intercoms. 
Key Features and Components of a Digital Door Phone:
- Outdoor Unit (Door Station):
- Camera: The outdoor unit includes a digital camera that captures the visitor’s image and sends it to the indoor monitor or device. Depending on the model, cameras may have features such as night vision, wide-angle lenses, or motion detection.
- Microphone and Speaker: These allow the visitor to communicate with the person inside the building. The microphone picks up the visitor’s voice, while the speaker lets the person inside hear the visitor clearly.
- Button/Access Control: The visitor can press a button to alert the resident. Advanced systems may include access control features like keypads for entering codes, fingerprint scanners, or even facial recognition for granting access.
- LED Display or Indicator: Some digital door phones also have an integrated screen or LED lights that display system status or alert users to a visitor’s presence.
- Indoor Unit (Receiver/Monitor):
- Digital Display Screen: The indoor unit typically features a high-definition screen to display a live video feed of the person at the door. The screen might be a touch screen or include physical buttons for control.
- Microphone and Speaker: These components allow for two-way communication between the resident and the visitor at the door.
- Control Buttons/Touch Interface: The indoor unit usually includes buttons or a touchscreen for answering the door, unlocking it remotely, adjusting volume, and managing settings such as video quality, brightness, and contrast.
A Wi-Fi Access Point (AP) is a networking device that allows wireless devices, such as laptops, smartphones, tablets, and other Wi-Fi-enabled devices, to connect to a wired network using Wi-Fi (wireless fidelity) technology. It acts as an interface between the wired network (like an Ethernet network) and the wireless devices, enabling communication over radio waves. 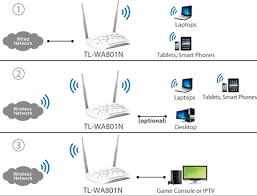
Key Features and Components of a Wi-Fi Access Point:
- Radio Transmitters/Receivers:
- Wi-Fi APs contain radio transmitters and receivers that use radio waves to send and receive data to and from Wi-Fi-enabled devices. The AP communicates using specific frequency bands, such as 2.4 GHz and 5 GHz, or even 6 GHz in the case of newer Wi-Fi 6E standards.
- Ethernet Port (Wired Network Interface):
- The AP is usually connected to a wired network, typically via an Ethernet cable. This Ethernet port is used to connect the AP to a router, switch, or hub, which is part of the broader network infrastructure.
- Network Processor and Software:
- Wi-Fi access points have processors that manage network traffic, handle data routing, and manage security features such as encryption and authentication protocols (like WPA2 or WPA3). Some APs may also include software for configuring and managing the network.
- Antenna:
- The AP may have internal or external antennas that help transmit and receive wireless signals. The placement and number of antennas affect the coverage area and performance of the AP.
- SSID (Service Set Identifier):
- The AP broadcasts the SSID, which is the network name that devices use to identify and connect to the wireless network. The SSID can be hidden or publicly broadcast, depending on the configuration.
- Power Source:
- APs can be powered using standard AC power adapters, or in some cases, Power over Ethernet (PoE) is used, allowing both power and data to be transmitted over the same Ethernet cable, reducing the need for additional power cables.
Types of Wi-Fi Access Points:
- Standalone Access Point:
- A single, independent AP that provides wireless coverage in a localized area. It’s typically used in small homes or offices to expand the reach of a router’s Wi-Fi signal.
- Controller-Based Access Point:
- These APs are managed by a central controller that helps optimize network performance, provide centralized management, and enforce security policies. This type of AP is common in enterprise networks where scalability and performance are important.
- Mesh Access Point:
- These APs are used in mesh networks, where multiple APs work together to create a seamless and extended Wi-Fi network across large areas. Each AP in a mesh network can communicate with others, providing wider coverage and reducing dead zones.
- Outdoor Access Points:
- Designed for outdoor use, these APs are weatherproof and have enhanced range, making them ideal for extending Wi-Fi coverage in outdoor spaces, campuses, or large properties.
Data Networking refers to the practice of connecting multiple computing devices, systems, or networks to enable communication and data exchange between them. It involves the design, implementation, and management of network systems, ensuring the efficient and secure flow of data across various types of network infrastructure. 
Key Components of Data Networking:
- Devices: These are the endpoints or nodes in a network, such as computers, servers, routers, switches, and other networked devices.
- Transmission Medium: This refers to the physical or wireless channels through which data is transmitted. Examples include copper cables (Ethernet), fiber-optic cables, and wireless radio signals (Wi-Fi, cellular networks).
- Protocols: Protocols define the rules and conventions for data exchange. Some key protocols in data networking include:
- TCP/IP (Transmission Control Protocol/Internet Protocol): The foundational protocol suite for most modern networks, especially the internet.
- HTTP/HTTPS (Hypertext Transfer Protocol): Protocol for web communication.
- FTP (File Transfer Protocol): Used for file transfer across networks.
- DNS (Domain Name System): Translates domain names to IP addresses.
- Routers and Switches: Routers direct data between different networks, while switches manage data traffic within a single network, ensuring devices can communicate with each other efficiently.
- Topologies: Network topologies define the layout and arrangement of network devices. Common types include:
- Star Topology: All devices are connected to a central node, often a switch or hub.
- Bus Topology: All devices are connected to a single central cable.
- Mesh Topology: Each device is connected to every other device, ensuring high reliability and redundancy.
- IP Addresses: Devices in a network are assigned unique identifiers, called IP addresses, that enable them to be located and communicated with across the network.
Laptop vs Desktop: Description and Comparison
Both laptops and desktops are personal computers used for a variety of tasks, but they differ in their design, functionality, and intended use. Here’s a detailed description of each, along with a comparison:
Laptop:
A laptop is a portable computer that integrates most of the key components of a desktop computer (such as the CPU, memory, and storage) into a compact, lightweight design. Laptops are designed for mobility, enabling users to work or access information while on the move. 
Key Features of Laptops:
- Portability: Laptops are designed to be lightweight and compact, typically ranging from 2 to 6 pounds. They come with built-in screens, keyboards, and trackpads or pointing devices, making them ideal for mobile use.
- Battery-Powered: Laptops have a built-in rechargeable battery that allows them to operate without being plugged into a power outlet for several hours, depending on usage and battery capacity.
- Integrated Components: Laptops combine a screen, keyboard, touchpad (or trackpoint), speakers, and camera into a single device. This makes them all-in-one solutions for portable computing.
- Smaller Screen Size: Laptop screens generally range from 11 inches to 17 inches diagonally, with 13–15 inches being the most common size.
- Connectivity: Laptops typically offer wireless connectivity options like Wi-Fi and Bluetooth, in addition to physical ports for USB devices, HDMI, and Ethernet (though these may be fewer than desktops due to the compact design).
- Battery Life: A major advantage of laptops is their ability to run on battery, making them ideal for travel and situations where power outlets are not available. Battery life can range from 4 hours to over 20 hours, depending on the model.
Advantages of Laptops:
- Portability: Ideal for users on the go.
- Built-in battery: Can work without a power outlet.
- Compact design: Saves space and can be used in various environments (coffee shops, airports, etc.).
Disadvantages of Laptops:
- Less power and performance options compared to desktops, especially for high-end gaming or professional applications.
- Limited upgradeability: Components like the processor, graphics card, and RAM are often not upgradeable.
- Smaller screens and keyboards, which might be less comfortable for long hours of work.
The combination of video content and data storage involves managing, storing, and retrieving video files within various types of storage systems. As video content often consumes significant storage space, understanding the relationship between video and data storage is crucial in both personal and professional contexts (e.g., media production, streaming services, video conferencing, or surveillance systems). 
Key Aspects of Video with Data Storage
- Video Files:
Videos are large digital files that can vary greatly in size depending on factors such as:
- Resolution: Higher resolutions (like 4K or 8K) require more storage space compared to lower resolutions (like 1080p or 720p).
- Frame Rate: Higher frame rates (e.g., 60 fps) demand more storage space than lower frame rates (e.g., 30 fps).
- Compression: Video files are often compressed using various formats (like MP4, AVI, MOV, or MKV) to reduce their size while maintaining video quality.
- Length and Quality: Longer videos and videos with higher quality (such as HD, 4K) require significantly more storage.
- Video Storage Requirements:
Storing video files requires substantial data storage resources. Video storage systems should be optimized to handle large file sizes, fast access, and high-throughput processing.
- Personal Use: For individual users, video storage needs might be met using external hard drives, cloud storage, or solid-state drives (SSDs). However, personal video storage is limited when compared to professional use.
- Professional Use: In industries such as film production, media, or surveillance, large-scale video storage systems are necessary to manage vast amounts of footage. These systems must support high data transfer rates, quick access, and redundancy to prevent data loss.
- Types of Video Storage Solutions:
- Local Storage:
- External Hard Drives (HDD): Common for personal video storage, offering large capacity at a lower cost. However, slower speeds compared to SSDs.
- Solid State Drives (SSD): Faster than HDDs, ideal for storing frequently accessed video files or for video editing. However, SSDs tend to be more expensive than HDDs per gigabyte.
- Network Attached Storage (NAS): A storage system connected to a network, providing centralized access to video files. Useful for small to medium-sized businesses or home use.
- Cloud Storage:
- Cloud Services like Google Drive, Dropbox, iCloud, or specialized services like Amazon S3 or Microsoft Azure allow for off-site storage of video files. Cloud storage is scalable and accessible remotely, but video files can be subject to upload and download speed limitations.
- Video Streaming Platforms: Video streaming services (e.g., YouTube, Vimeo) provide cloud-based video storage and access for sharing and viewing videos.
- Enterprise Video Storage Solutions:
- Storage Area Networks (SAN): Large-scale storage solutions used by enterprises, providing high-speed data access and large-scale video storage, often used in media production environments.
- Object Storage: Used for storing unstructured data like videos, ideal for cloud-based video storage solutions. Examples include Amazon S3, Google Cloud Storage, and Microsoft Azure Blob Storage.
- Tape Storage: Often used for long-term archival of video content. Though it has slower access speeds, it’s cost-effective for large volumes of video data that aren’t frequently accessed.
A boom barrier system (also known as a boom gate or barrier gate) is a mechanical gate commonly used for controlling access to vehicles at entry and exit points, such as parking lots, toll booths, gated communities, industrial sites, and airports. The system typically consists of a long horizontal bar (the “boom”) that can be raised or lowered to permit or restrict the passage of vehicles.
The boom barrier system is widely used in applications where controlling the flow of traffic or securing restricted areas is necessary. 
Key Components of a Boom Barrier System:
- Boom Arm:
- The boom arm is the primary moving part of the system. It is a long, rigid bar that swings up or down to allow or block vehicle entry.
- Materials: Booms are typically made from durable materials such as steel, aluminum, or fiberglass, and they may have reflective strips or lights for visibility.
- Length: Boom arms usually range from 2 meters (6.5 feet) to 8 meters (26 feet), depending on the width of the area to be controlled (e.g., one or two lanes).
- Barrier Box/Controller Unit:
- The controller unit houses the mechanism that controls the boom’s movement, as well as the electronic components for operating the system.
- Drive Mechanism: This includes motors, gears, and shafts that control the raising and lowering of the boom.
- Sensors and Controls: The system may have sensors to detect the presence of vehicles and to automate the process of opening or closing the boom. There may also be manual controls for operators.
Visitor Management System: Description and Overview
A Visitor Management System (VMS) is a digital solution used by organizations to streamline and control the process of visitor registration, access, and tracking. It provides a structured way to manage visitors who come to a company or facility, ensuring both security and efficiency. A VMS typically replaces traditional paper-based logbooks, improving accuracy, data collection, and the overall visitor experience. 
Key Features of a Visitor Management System:
- Visitor Registration:
- Pre-Registration: Some VMS allow visitors to pre-register online before their visit, entering details like their name, purpose of visit, date, time, and the person they are visiting. This can expedite the check-in process on the day of the visit.
- On-Site Registration: Upon arrival, visitors can check in via self-service kiosks, tablets, or desktop computers. The system collects necessary information, such as name, photo, identification, and the host they are meeting.
- Identification and Badging:
- Visitor Badges: A key feature is the creation of a visitor badge. The VMS generates a badge for each visitor, often with their name, photo, time of visit, and the host’s details. Badges may also include barcodes, QR codes, or RFID tags for easy scanning and tracking.
- Digital Signatures: Some systems require visitors to sign in digitally, either to acknowledge the terms of their visit or to provide an electronic signature for added security.
- Host Notification:
- Automatic Alerts: When a visitor arrives and completes their check-in, the system automatically notifies the host via email, text message, or through the internal communication system. This ensures the host knows when their guest has arrived and can meet them promptly.
- Host Approval: In some systems, hosts may have to approve or authorize visitors before they can enter the premises, adding an additional layer of control.
- Security and Access Control:
- Access Control Integration: Many modern VMS are integrated with access control systems (like key cards, biometrics, or RFID scanners) to restrict or allow visitor access to certain areas within the facility. The system ensures visitors only go to the areas they are authorized to enter.
- Visitor Tracking: The system tracks visitors while they are on the premises, recording their entry and exit times. Some systems also track movements throughout the building, offering an audit trail for security purposes.
Entrance Gate Security System: Description and Overview
An Entrance Gate Security System is a security solution designed to control and monitor access to a building or facility through its main entrance gate. It combines various technologies and mechanisms to ensure that only authorized individuals or vehicles can enter the premises, providing both physical and digital layers of security. These systems are commonly used in residential complexes, corporate offices, government buildings, industrial facilities, and critical infrastructure sites. 
Key Components of an Entrance Gate Security System:
- Gate Barrier or Gate Mechanism:
- Automatic Gates: These gates open and close automatically upon receiving a signal from the authorized user. They can be sliding gates, swing gates, or roller gates. These systems are typically motorized and can be operated via remote control, access card, biometric scanners, or other methods.
- Manual Gates: Less common in modern systems, manual gates require human intervention to open or close, but they may still include locks or security bolts for additional protection.
- Access Control Systems:
- Keypads and PIN Code Entry: Users input a code to gain access. This method is commonly used in small to medium-sized facilities.
- RFID (Radio Frequency Identification): Visitors or authorized personnel use RFID cards or key fobs to trigger the gate opening. RFID systems are commonly used in parking lots, gated communities, and office complexes.
- Biometric Authentication: More secure than traditional methods, biometric systems use fingerprints, facial recognition, or iris scans to authenticate individuals. These are ideal for high-security areas.
- Keycard or Proximity Cards: Employees or authorized users carry access cards that use magnetic strips or chips to trigger the gate opening when scanned at the reader.
- Mobile Access: In modern systems, smartphones can serve as access keys using Bluetooth or NFC (Near Field Communication) technology to unlock gates.
- Security Cameras (CCTV):
- Surveillance Cameras: Security cameras monitor the entrance area, recording the activities of people or vehicles trying to access the premises. They are often integrated with other security systems to provide real-time monitoring and footage for later review.
- License Plate Recognition (LPR): Some systems include cameras equipped with LPR technology to automatically read and log vehicle license plates, allowing authorized vehicles to enter without the need for a manual check.
Online/Offline UPS System: Description and Overview
A UPS (Uninterruptible Power Supply) is a device that provides backup power when the main power source fails. It ensures that critical devices (such as computers, servers, medical equipment, and industrial machinery) continue to operate without interruption. There are two primary types of UPS systems: Online UPS and Offline UPS, each designed to serve different power protection needs based on the level of criticality and cost considerations. 
- Offline UPS System:
An Offline UPS (also called a Standby UPS) is the simplest and most basic type of UPS system. It provides backup power to the connected devices when the primary power source fails or becomes unstable.
How It Works:
- Normal Operation (AC Supply): Under normal conditions, when the main power is available, the UPS remains idle. The connected devices draw power directly from the main supply, and the UPS keeps its internal battery charged.
- Power Failure (Battery Backup Mode): When there is a power failure or significant voltage fluctuation, the UPS quickly switches to its internal battery to provide power. The transition typically takes a few milliseconds (usually 5 to 10 milliseconds), which is enough to prevent the connected equipment from shutting down, although sensitive devices may notice a slight disruption.
Key Features of Offline UPS:
- Basic Protection: Primarily protects against power outages, voltage sags, and surges.
- Switching Time: Slight delay (usually milliseconds) when switching from mains to battery power, which may cause a brief flicker in sensitive equipment.
- Cost-Effective: Offline UPS systems are typically less expensive compared to online systems.
- Ideal Use Cases: Best for home offices, personal computers, and small businesses with less critical loads where power interruptions are infrequent or short in duration.
Advantages of Offline UPS:
- Affordable: Less costly, making it suitable for smaller applications.
- Compact: Generally smaller and lighter than online UPS systems.
- Energy-Efficient: Since the inverter is inactive in normal operation, these systems are more energy-efficient.
Disadvantages of Offline UPS:
- Limited Power Quality Protection: It cannot regulate voltage fluctuations or provide clean power continuously.
- Switching Time Delay: The delay in switching to battery mode can lead to issues for sensitive equipment during a power failure.
- Online UPS System:
An Online UPS (also called a Double Conversion UPS) offers a higher level of protection for sensitive equipment by continuously providing power from the battery and filtering the incoming electrical supply. Unlike the Offline UPS, which relies on a battery only when the main power supply fails, the Online UPS provides power through its inverter at all times, ensuring continuous power supply without any interruption.
How It Works:
- Constant Power Supply (Double Conversion Process): The Online UPS system continuously converts incoming AC power to DC power through the rectifier. This DC power is then converted back into clean AC power by the inverter and supplied to the connected devices. Even when the main power supply is available, the UPS filters and conditions the power, ensuring that the devices receive a constant, stable voltage.
- Power Failure: In case of a power failure or any abnormality in the main supply (such as power surges or voltage dips), the UPS continues to supply power from the battery without any delay. The transition is seamless, and no power disruption is experienced by the connected load.
Key Features of Online UPS:
- Continuous Power Supply: Provides uninterrupted, clean, and conditioned power to devices at all times.
- Double Conversion: The double conversion process helps in regulating voltage, filtering noise, and eliminating any distortions in the power supply.
- Ideal for Sensitive Equipment: Suitable for applications where a continuous power supply and high-quality power are critical, such as servers, data centers, medical equipment, and industrial machines.
Advantages of Online UPS:
- Zero Transfer Time: There is no transfer time when switching to battery power, making it ideal for sensitive or mission-critical equipment.
- Power Conditioning: Filters and stabilizes incoming power, providing protection from power surges, spikes, and sags.
- Continuous Operation: The connected devices experience no interruptions in power supply, even during power disturbances or failures.
- Advanced Protection: Offers comprehensive protection against power anomalies, including voltage fluctuations, harmonics, surges, and noise.
Disadvantages of Online UPS:
- Cost: Online UPS systems are more expensive than Offline UPS systems due to their advanced features and continuous operation.
- Heat Generation: Since the inverter is always in operation, Online UPS systems tend to generate more heat and may require additional cooling solutions.
- Size and Weight: Typically larger and heavier than Offline UPS systems, making them less suited for small spaces or personal use.